Clock In Restrictions
By default, employees can log in from any location with an internet connection. Clock In Restrictions allow you to block log ins from areas that have not been authorized.
Summary
IP Address — Uses the network IP address
Subnet Group — Uses the network IP address, but broadens the restriction to accommodate a rotating IP address (rotating IP's are not common)
Vault — A downloadable program that runs through Microsoft Edge and is unlocked with a password
Authorized Browser — Unlock designated browsers on one or more computers using a password
*See Mobile section for Mobile App GPS restriction
Setup menu: Clock In Restriction
IP Address
Access is based on the IP Address of your router. Anyone who can connect to your office WiFi (including cellphones!) will be able to log in.
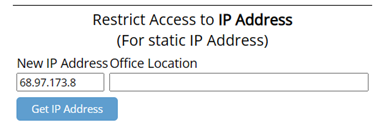
If you are connected to the IP address you want to authorize, click "Get IP Address."
If you are not connected to the IP address you want to authorize, type the IP address in the text box.
If you do not know the IP address you need to authorize, you may be able to get it from the Access Report, in the Reports menu (see Address below).
FAQ About IP Address
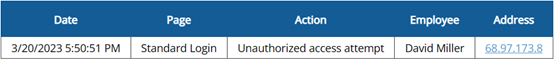
How can I view the IP address my employees are attempting to log in from?
In the Reports menu, the Access Report logs all activity. Try searching the word “Unauthorized” to find the lines for unauthorized access attempts.
I’ve been using the IP address restriction for a while, but now my employees are seeing “Unauthorized Access” when they try to log in…
Your IP address has probably changed. When the internet is shut off due to a change in service, repairs, or even a reboot, a new IP address may be assigned to the modem. When this happens, just replace the old IP address with the new one in the Clock In Restriction page.
Subnet Group
This option is for very specific companies that have a designated range of IP addresses.
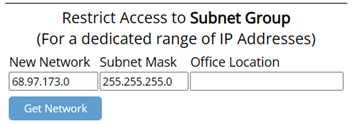
Connected to the network you want to authorize, click "Get Network."
FAQ About Subnet Group
How do I know whether I should use IP Address or Subnet Group?
Subnet Group should only be used if your company uses a dedicated range of IP Addresses, which is not common. In most cases, IP Address is the best option.
The IP addresses keep changing the last 2 sets of numbers. Can I broaden the restriction?
This will make the restriction less secure, but you can broaden the subnet group. Replace the third set of numbers in the Network and the Subnet Mask with “0.” The 0 allows that set of numbers to vary.
![]()
![]()
![]()
Authorized Browser
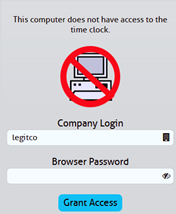
Grant access to a specific browser on each computer with a password you create.
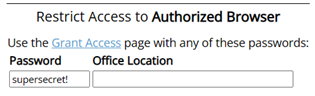
If you're on the device/browser you want to unlock, click Grant Access.
Set your own password in the Password field and enter it on the Grant Access page (seen below).
FAQ About Authorized Browser
How can I restrict how many times an employee can use the password?
There are no usage limits on the Authorized Browser restriction, so we suggest entering the password yourself to unlock browsers, rather than sharing the password with your employees.
Why did the computer clear the password?
If the cache is cleared on the browser, the password will need to be entered again.
Vault
This restriction is limited to PC computers. This downloadable program is a Microsoft Edge emulator that requires a password to unlock.

If downloading Vault onto the computer you're using now, click the Download Vault Here link (above) to download the .exe file.
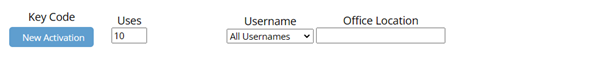
Step 1: Click New Activation (above).
(If you already see a Show Key Code button, you may not need to activate a new Key Code.)
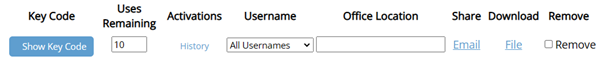
Steps 2-5 reference the above image.
Step 2: Click Show Key Code.
Take note of the 4-digit password, if downloading the program yourself.
Step 3: Change Uses Remaining.
If you need to download to more than 10 computers, or if you want to make sure employees don't unlock computers that shouldn't be authorized, change the number to a smaller or larger amount.
Step 4: Set Username to a username or keep All Usernames.
All Usernames allows the program to let any of the employees log in with that Key Code. By setting to an individual username, the program won't let anyone else log in from the computer the Key Code is used on.
Tip: Keeping All Usernames usually requires less maintenance.
Step 5: Send to Employees.
Under Share, click the Email link to generate an email with download instructions and the Key Code for you to send to employees.
FAQ About Vault
Can I use Vault on a Mac computer?
Vault is not compatible with Mac. Authorized Browser is the suggested alternative.
Why is a new computer not taking the Key Code we’ve always used?
As the Key Code is used to unlock Vault on each device, the “Uses Remaining” goes down. On the Clock In Restriction page, if you see a “0,” you will need to allow more uses by adding a larger number and saving.
How do I change the username that shows on the Vault login page?
If you find an employee’s name is hardcoded into the Username field but you need a new employee to use it, go to the Clock In Restriction page, find the old employee’s name and use the dropdown menu to choose the new employee. Close and reopen the Vault program.
Watch Video:
